Edit
Wannacrypt
The NSA's hack on old Microsoft operating systems is weaponised and released to the internet, most publicly massively impacting the UK's NHS, which had taken the decision not to move forward from Windows XP, a product for which support by its authors ceased in 2012.
- This was meant to be quick and a source list for a blog article, but as ever it took too long.
- An internet worm was unleashed on the internet over the weekend, implementing a ransom attack. The target and propagators are/were old systems of Windows, specifically those that Microsoft no longer supported: XP, Vista and Windows Server 2003.
- This was reported in the BBC, the Register, and by Glynn Moody
 NHS cyber-attack: GPs and hospitals hit by ransomwareAmbulances are diverted and appointments cancelled as a ransomware infects NHS computers.
NHS cyber-attack: GPs and hospitals hit by ransomwareAmbulances are diverted and appointments cancelled as a ransomware infects NHS computers.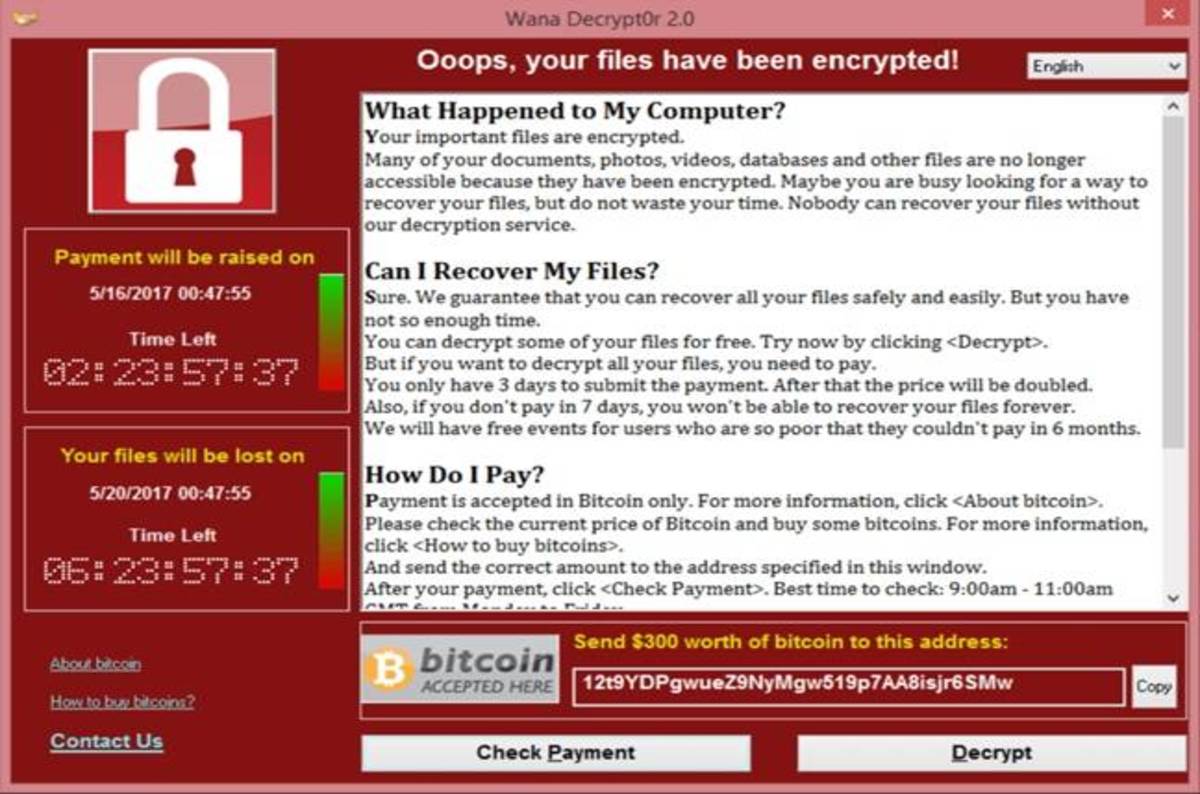 74 countries hit by NSA-powered WannaCrypt ransomware backdoor: Emergency fixes emitted by Microsoft for WinXP+All you need to know – from ports to samples
74 countries hit by NSA-powered WannaCrypt ransomware backdoor: Emergency fixes emitted by Microsoft for WinXP+All you need to know – from ports to samples#NHS left reeling by-attack: ‘We are literally unable to do any x-rays’ - htt...
#NHS left reeling by-attack: ‘We are literally unable to do any x-rays’ - https://www.theguardian.com/society/2017/may/13/nhs-cyber-attack-patients-rans... - glyn moody - Google+- Ross Anderson, one of, if not the, UK's leading civil IT security researcher[s] is a bit more sanguine about the impact and catalogues some of the news stories inaccuracies,
Bad malware, worse reporting | Light Blue Touchpaper
The Wannacry malware that has infected some UK hospital computers should interest not just security researchers but also people interested in what drives fake news.- He also deals with the intelligence services culpability,
- Many papers caught the international political aspect: that the vulnerability was discovered by the NSA, kept secret rather than fixed (contrary to the advice of Obama’s NSA review group), then stolen from the CIA by the Russians and published via wikileaks. Scary stuff, eh? And we read of some surprising overreactions, ....
- Ars Technica reports in two stories,
Wanna Decryptor ransomware appears to be spawning and this time it may not have a kill switch
Wanna Decryptor 2.0 (wana decryptor/wncry), linked to NHS cyber attack was fixed with MS17-010 patch but may have mutated Wanna Decryptor ransomware: What is it, and how does it work?Wcry (aka Wanna Decryptor) uses weapons-grade exploit originally discovered by the NSA and leaked by Shadow Brokers.
Wanna Decryptor ransomware: What is it, and how does it work?Wcry (aka Wanna Decryptor) uses weapons-grade exploit originally discovered by the NSA and leaked by Shadow Brokers.- But Amber Rudd, who is leading politically for the government suggests that patient records may have been lost
 Amber Rudd says patient records may have been lost in NHS cyber attackAmber Rudd has said NHS patients' files could have been lost after an unprecedented cyber attack saw medical staff locked out of test results, X-rays and patient records. The Home Secretary said she “hoped” data would be retrievable, but that “holes” in the back-up systems are likely to emerge in the coming days.
Amber Rudd says patient records may have been lost in NHS cyber attackAmber Rudd has said NHS patients' files could have been lost after an unprecedented cyber attack saw medical staff locked out of test results, X-rays and patient records. The Home Secretary said she “hoped” data would be retrievable, but that “holes” in the back-up systems are likely to emerge in the coming days.- And because I was so slow to publish, I get to share this, which says its W7 that was the problem, not XP; shame for me with the anti-Tory agenda.
 Wannacry: Everything you still need to know because there were so many unanswered QsHow it first spread, Win XP wasn't actually hit, and more
Wannacry: Everything you still need to know because there were so many unanswered QsHow it first spread, Win XP wasn't actually hit, and more- I should add that W7 was supported and the patch was therefore available. This i a problem with patching policy not necessarily money.
- The source of the code that caused this catastrophe would seem to have been leaked/stolen from the NSA. I mention this above, but the story was also reported by the Register,
 Shadow Brokers crack open NSA hacking tool cache for world+dogDaaaamn, these exploits are old-school
Shadow Brokers crack open NSA hacking tool cache for world+dogDaaaamn, these exploits are old-school- Microsoft released patches for their supported OS's once the shadow brokers released the hack; they fixed the vulnerability on the systems that they stated they were issuing security patches for, and over the weekend they actually back ported it to XP & W7.
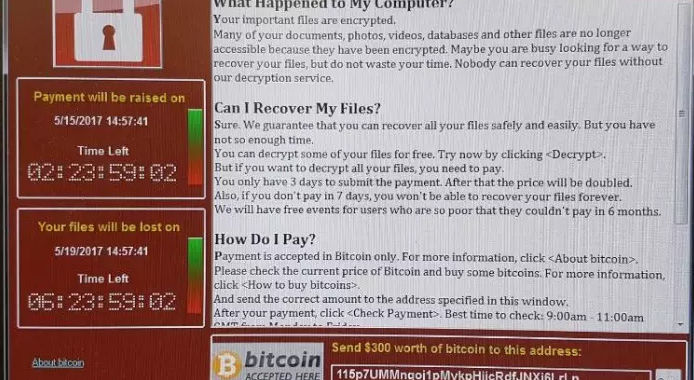 Wanna Decryptor is so mean Microsoft issues patch for three unsupported Windows versionsWindows XP, 8, and Server 2003—decommissioned for years—get emergency update.
Wanna Decryptor is so mean Microsoft issues patch for three unsupported Windows versionsWindows XP, 8, and Server 2003—decommissioned for years—get emergency update.- The ORG points at GCHQ's role in all this, as they criticise the lack of a plan from the theft.
 NHS ransom shows GCHQ putting us at riskThe NHS ransom shows the problems with GCHQ’s approach to hacking and vulnerabilities, and this must be made clear to MPs who have given them sweeping powers in the IP Act that could result in the same problems recurring in the future.
NHS ransom shows GCHQ putting us at riskThe NHS ransom shows the problems with GCHQ’s approach to hacking and vulnerabilities, and this must be made clear to MPs who have given them sweeping powers in the IP Act that could result in the same problems recurring in the future.- The decision that the NHS stay on XP and WS2003 was deliberate and based on cost, we cannot know if a cost based risk assessment was taken.
- Old systems are more vulnerable because people have more time to find the weaknesses and at some point the authors/copyright owners stop fixing vulnerabilities.
- The Mirror covers the NHS Management and political culpability here .... , as does the Guardian.
 Jeremy Hunt 'ignored warning signs' before cyber-attack hit NHSShadow health secretary says concerns were repeatedly flagged about outdated computer systems that are vulnerable to attack
Jeremy Hunt 'ignored warning signs' before cyber-attack hit NHSShadow health secretary says concerns were repeatedly flagged about outdated computer systems that are vulnerable to attack- Sky also covers this, although the headline is misleading since the patch for the vulnerable operating systems was not available until this week.
 NHS cyberattack: Trusts were told about security patch last monthNHS England hospital trusts were sent details of a security patch that would have prevented the malware attack last month.
NHS cyberattack: Trusts were told about security patch last monthNHS England hospital trusts were sent details of a security patch that would have prevented the malware attack last month.- Tim reports that Amber Rudd, of hashtag fame, suggesting that patient records may have been lost compounding the availability failure. (See above also).
 D'oh! Amber Rudd meant 'understand hashing', not 'hashtags'Home Sec sends out junior minister to clarify gaffe
D'oh! Amber Rudd meant 'understand hashing', not 'hashtags'Home Sec sends out junior minister to clarify gaffe Amber Rudd’s NHS IT ShameToday’s papers are almost of one voice on their lead stories: there has been a cyber attack on organisations across the world, which i...
Amber Rudd’s NHS IT ShameToday’s papers are almost of one voice on their lead stories: there has been a cyber attack on organisations across the world, which i...- Standard good practice states the importance of applying vendor security patches and abandoning out of date software. These are key controls specified as part of ISO 27001, it's not as if we don't know how to prevent this attack. Regulated industries are asked if they perform this work and fined or sanctioned if they don't. The lesson for all CIOs (and Boards) is to take full spectrum IT security seriously, this is not a-la-carte dining where you only have what you want ... defenders have to be right all the time, the bad guys only have to get it right once, and this case they had some very well equipped helpers. The second lesson is that Governments are no better at keeping your secrets than you are, proven by the fact that the code seems to have come from the NSA. Probably best not to give them legal privilege and backdoors to perform activities which would be illegal if conducted by private individuals or companies.
- ISO 27001 12.6 specifically refers to operations security and mandates the use of up to date software.
- If this were a private sector concern, then the regulators would be asking why the decision was taken, in the case of all industries the Data Protection Act requires that systems have adequate technical protection against availability failures, and in large banks such actions would also lead to failures in their "Living Wills" compliance.
- I am somewhat sad that I can't embed Medium articles, but this by John Elliot also explain how we got here and sets out the questions to be answered.
- Let's start to finish on a slightly lighter note, the IT Crowd recognised the weakness in Microsoft Vista.
- But more scarily another version of an old Windows product is used to run Britain's Nuclear Deterrent. Another proof point that the NSA should have told Microsoft, and that failing to do so jeopardises, well, everyone.
 Britain's Doomsday Nuke Subs Still Run Windows XPThe fate of the country's nukes is in the hands of an obsolete operating system.
Britain's Doomsday Nuke Subs Still Run Windows XPThe fate of the country's nukes is in the hands of an obsolete operating system.
