Dyndns don’t do free anymore. Bother! Not for four years or so, shows how much interest I have taken. …
Data Protection
Over the last couple of days, I have posted two articles to my linked in blog, one on the nature of pictures/images as personal data (it is, it’s also special), the earlier is on my 5 things to do for GDPR compliance. …
Bitcoin
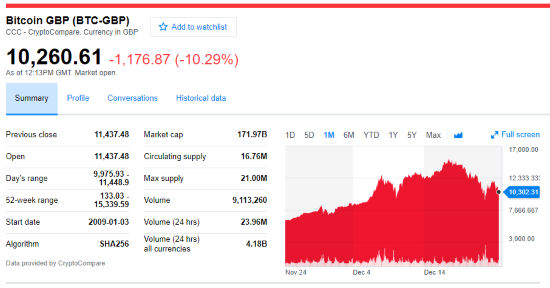
This is a long diatribe at Hacker Noon about the Bitcoin bubble and the blockchain hype. I had been considering writing something similar although my focus was on the excessive use & cost of electricity to “mine” coins and the demonstrable industrialisation and economic consolidation of the mining operations.
Bitcoin, in particular, has a shrinking use as a means of exchange, as identified by this business insider preview of a Morgan Stanley opinion. This is compounded by the fact that the transaction fees are now too high for small or micro payments, and that it is not real time, (it can take minutes to clear) and thus cannot be used for transactions that require simultaneous exchange, be it a cup of coffee or a house.
The block chain does not scale well, despite the massively distributed architecture. If its performance is matched with say Visa or other significant global payment processors, VISA is rated at 60,000 transactions/sec (TPS) where as the Bitcoin maxes out at 7 TPS. So not only is it expensive, but it can’t cope with real world volume; it’s just as well that small transactions are deserting the platform.
What started me thinking this time round, was the realisation that the amount of power required to “mine” the currency grows and is now significant. While the compensation for the miners is scrip/free, the real cost in electricity and thus carbon pollution is significant. This adds to the cost, both internal but more importantly the external cost. The planet cannot afford the electricity power and the carbon footprint to virtualise global capitalism’s money supply.
Kai Stinchcombe argues that the lack of regulation is also a disincentive to use crypto currencies and examines the Etherium/DAO hack and draws the conclusion that on the whole society needs contracts to be interpreted by people, not by software.
Money must be a means of exchange, and a store of wealth, block-chain crypto-currencies are struggling and increasingly failing to be the former and it’s current price peaks , historic volatility and lack of regulator suggests it’s weak as the latter. Is it just a con? …
E-Voting

At my last Union branch meeting, we heard from Gemma Short of the right to strike campaign. As one part of her presentation she mentioned that one of the Unions’ response to the recent Trade Union laws is to demand that they can run strike ballots (and the mandatory political levy and elections) using e-voting technology. I have been thinking about this for a while and its fans need to take stock; there’s some inconvenient truths. …
Search Prominence in Politics
In 2011, Andrew Rhodes wrote a paper entitled, Can Prominence Matter Even in an Almost Frictionless Market? He models consumer behaviour in frictionless markets and the role of search engines and their paid placement on the search results page. I have had a look at the article because I am the target of one of Lewisham Labour’s candidates for Mayor’s google ad-campaign. I look at what Rhodes did, and ask a couple of questions about how applicable his model and assumptions are. …
Sunset, finally?

Simon Phipps comments on Oracle’s decision to close down the SPARC and Solaris business units. He was close to the politics of Sun’s “Dash to Open” in the mid noughties. My feeling is that Sun had failed before Schwartz was appointed; there was no longer room for differentiated hardware company; Oracle’s failure to monetise the SPARC product line may have been caused by management hubris, but the long term economics …
The coming Data Protection Officer, needed, expert & independent

A presentation was made about the to be established Data Protection Officer, claiming to be informed by the EU’s advice on what the law means. We looked at whether a DPO is needed, the expertise and skills required, and the requirement for independence. …
An overview of issues with the GDPR

At the BCS legal day, a presentation was made entitled “Key Issues” which they started with a quote from Jan Albrecht MEP (the Rapporteur),
“[The] result is something that makes (as we intended from the beginning) everybody equally unhappy, but at the same time is a huge step forward for all sides involved.
Jan Albrecht MEP”
It is hoped that business opportunity will be created by a harmonisation of regulation across Europe with a goal of improved privacy for its citizens. The harmonisation is constrained by the Restrictions Article, which excludes areas of law from the Regulation and creates nationally authored variances. …
BCS Legal Day

I attended the BCS ISSG Legal day where the priority was the coming General Data Protection Regulation. I believe that the day was held under Chatham House rules, which means that comments cannot be attributed. I prefer to work on more open terms; it allows me to attribute credit to those who have informed me or changed my mind but the notes have been anonymised. The running order has been changed to make the story better and to conform to my preferred priority order, of principles, rights, obligations and enforcement. The day consisted of two presentations, entitled “Key Issues”, “the Data Protection Officer” and one on trends in enforcement. I have written these notes over the last week, and backdated them to the day of occurrence. These are a bit less polemic than my recent articles here, but for various reasons I have been reminded that that’s how they once were; I hope these articles are useful to my more technical readers. Some of the discussions and issues may interest those that follow me for politics. …
A note on IT Integrity and authority
I posted an article that had taken a long time to get approval for on my employer’s blog, Information Integrity, the final frontier. I argue that the business has not taken integrity as seriously as it has availability and confidentiality. In the blog, I state that,
Information integrity requires an accurate representation of the state of the business and the audit records as to how it got there. Modern systems need to record both; it’s not enough that the system is provably accurate, records are required to ensure that transactions and changes are appropriately authorised.
The key insight is that not only must the true state of the data be recorded but that the person verify this truth must be recorded.
The article talks about strong “Requirements Management” and good “Testing” processes, and then talks about the use of PKI to sign application to application feeds or transactions to guarantee to the system of record that the author is a permitted actor and that the delivered data is accurate and authorised. I also propose that application logs as proposed under the “Application Security” domain of ISO/IEC 27034 should be used to record the authority/author of a database update.
ooOOOoo
Given the startling longevity of this blog, I have made a mirror of the Citihub article and loaded it to this site; integrity: the final frontier, a mirror …